Encoding vs encryption for 📱iOS app devs
Anyone can install your app from AppStore, decrypt and decode it — and read the data you stored there in a plist. Watch @Anastasiia Voitova (@Cossack Labs) and @Vincent Pradeilles disclosing how to secure your users’ data.
The truth is any data you add to your mobile app when developing can be readable because it's a part of an application bundle. Every single part of your application bundle is public information. And all the info you put there massively affects all the app’s users. So, every secret you put there can reveal your app users’ secrets.
What are the solutions?
⚫ If you want to store a particular session/token for the user that your application received during a transition to a backend, you should put it into a keychain at runtime.
⚫ If you want to hide some information/tokens that you received in advance while building an application, the good way is to use obfuscation or encryption — probably the easiest is to split the token and not put it as one string.
Watch this video to get in detail:
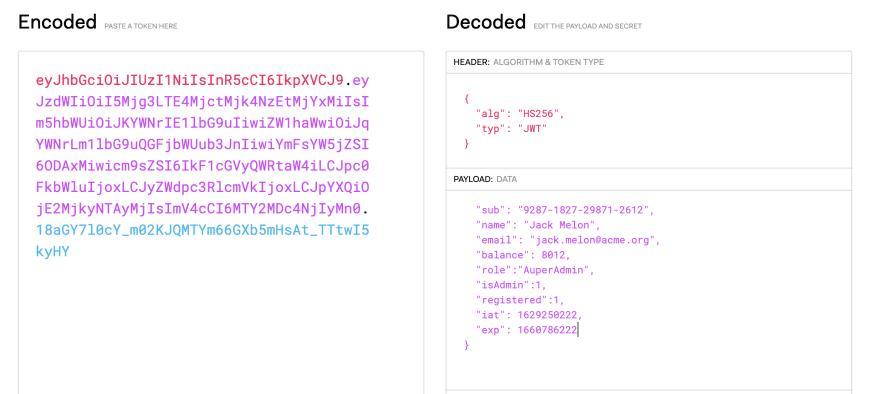
Often, plaintext data looks encrypted while it’s just encoded. For example, in JWT tokens. Any JWT token is a json encoded in base64 format.
So, all fields that you add there — email, name, account role, account balance – is stored in plaintext, just encoded but not encrypted. Use sites like jwt.io to find out the token content.
💡 Here’s a solution:
To avoid revealing sensitive information, don’t put it in JWT — for example, use user ID instead of user email. Also, make sure that all things that look like encrypted, are really encrypted.
Say hi 👋 to Anastasiia and Vincent!
Follow us for more data security tips and news:
🔥https://www.cossacklabs.com/
🔥https://twitter.com/cossacklabs
🔥https://github.com/cossacklabs
🔥https://www.linkedin.com/company/cossack-labs/