.NET Core and How-to Configuring HTTPS in ASP.NET Core
With the immense popularity of .NET Core, more and more organizations are developing and migrating their business applications. Regardless of its scalable architecture and robustness, it offers a highly secure environment to assure data confidentiality, integrity, and availability. In addition, several inbuilt modules, functions, and components are present in the .NET package manager, which precisely aids to allow data transaction between only authorized users.
UseHttpsRedirection is one component of the .NET framework responsible for ensuring data flow seamlessly and securely. To learn more about the security element, keep reading further and know its basics along with the configuration procedure.
HTTPS Redirection and .Net Core
Whenever an Asp.NET application is developed, HTTPS protocol is enabled by default for security purposes and to ensure that the man in the middle, spoofing cookies, stealing, and eavesdropping attack is successfully prevented.
In addition, it is a redirection middleware to ensure that all the data is communicated over a secure network. In simple terms, it enforces the data to redirect from HTTP to HTTPS for using the cryptographic mechanism to maintain data integrity.
When this middleware is implemented, a 307 temporary redirect response is created, and it gets linked with the configured HTTPS port to define the path to the endpoint. In addition, there can be cases when HTTPS port is not specified, and some probability is evaluated of a privacy breach. For solving this drawback, .NET is upgraded, and its features are extended to avail the port details from an environment variable, known as HTTPS_PORT.
Further, if both the conditions are not specified in the ASP.NET application, the UseHttpsRedirection middleware will display a warning to the user, and no data will be forwarded. Therefore, it is necessary to implement this component in every .NET Core software for a smooth, seamless, and secure experience.
Why is UseHttpsRedirection necessary?
Let’s look at how the user is benefitted by enabling this element in the ASP.NET business solution.
- An encrypted transmission channel is created between the client and server system to maintain data integrity.
- Both client and server systems send acknowledgment before establishing a connection, allowing only authorized users to access the resources.
- Potential cyber-attacks, such as eavesdropping and spoofing, are prevented.
- All the data is transmitted securely, enhancing the user’s trust over the application and the organization.
- If the HTTPS protocol is not enabled, the user is warned to send data over the insecure network.
The Procedure to Configure HTTPS in ASP.NET Web App
It is essential to know how to configure HTTPS in ASP.NET applications, as providing a secure ecosystem to access resources and perform operations is a top priority of any business solution. You can follow the below-listed process to implement the HTTPS protocol successfully.
The architecture of ASP.NET has an incorporated class known as UseHttpsRedirection, which is the primary element utilized for securing the application. It redirects a response to the client if a request is forwarded through an insecure or HTTP configured network.
In addition, the developer can enable this attribute for both per-controller and per-action basis, as per the business requirements and defined project scope. However, it is preferred to allow it over the overall web application, and as a result, it will enforce every individual data chunk to go through the HTTPS channel.
The ASP.NET developer must define the below line code under the RegisterGlobalFilters method placed inside the FilterConfig class.
The RegisterGlobalFilters method is called and executed along with the Application_Start, as it is the primary method when the user starts the app. By applying this filter function, only HTTP requests passed to controllers will be enforced, and the user will still be allowed to access static files over an insecure communication channel.
To overcome the issue in RegisterGlobalFilters, you can use relative links to reference resources from the HTML. Furthermore, absolute URLs can also be used along with HTTPS protocol to assure the security of the overall ASP.NET solution.
Moreover, rewrite code can be modified, and data redirection can be configured at the reverse proxy level during the implementation of IIS. It will automatically alter the direction of incoming requests to the HTTPS-enabled network. The Web.config file needs to be saved with the below-provided code.
After compiling and adding this code to IIS, every bit of incoming traffic will be evaluated and handled precisely by moving it onto the secure channel connected to the ASP.NET application.
Securing the .NET Core
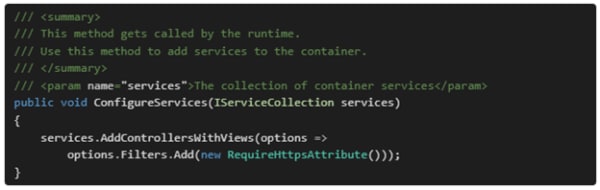
Creating a secure environment for transmitting data in a .NET Core app is not a complex task, as it offers an in-built class called RequireHttpsAttribute for preventing cyber threats.
With the aid of this class, you can configure security mechanisms over a single controller, action, or general application. You have to define it under the ConfigureServices method inside the Startup class.
In addition, an incorporated middleware, HTTPS Redirection, can also be configured through a single line of code, which you have to add in the Configure method of the Startup class.
app.UseHttpsRedirection(); is a single line code, which you have to write under Configure method to secure .NET Core solutions.
Moreover, you don’t always have to configure this middleware, as most ASP.NET web app templates, such as MVC, come with it by default enabled with it.
Here the question arises, what makes HTTPS Redirection middleware a preferred choice rather than RequireHttpsAttribute?
The overall credit for improved and optimized functioning of this middleware goes to the way .NET Core solutions are hosted. It aids in providing a higher level of security and redirects requests for static files from HTTP to HTTPS protocol-enabled channels.
Tightening the Security with HSTS
Till now, we have secured an ASP.NET application, but what if someone finds a vulnerable loophole and breaches your data.
To prevent malicious activities over your business solutions, .NET Core offers HSTS, a modular middleware component, which you can implement in a line of code.
HSTS stands for HTTP Strict Transport Security, and it is considered a more secure mechanism than HTTPS.
When an application is configured with only RequireHttpsAttribute, client requests are directly received by the app, and then it is redirected into the secure channel connecting to the server. HSTS leads to patch this vulnerability, as it informs the browser to allow app access only over HTTPS-enabled communication channels.
Functioning of HSTS
The core functioning of HSTS includes the Strict Transport Security header, which is returned in the response message. Further, the browser process this instruction and assure that all the upcoming user requests are transmitted through an HTTPS-configured connection.
As a result, no more redirects are executed, and all the data is security channelized.
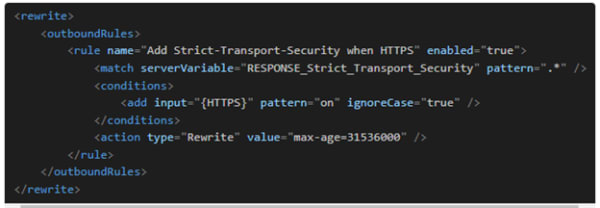
In addition, you can also configure HSTS at a reverse proxy level by defining the Outbound Rules. The only condition you have to fulfill is to run your application on an IIS server.
You have to write your outbound rules in the Web.config file and your application will be all set with HTTPS for secure data flow.
Implementing secure channel for APIs
APIs are an essential component of every application, as they are responsible for maintaining and connecting frontend elements with the backend for providing seamless user experiences.
Here the question arises: If we have configured RequireHttpsAttribute and HSTS for overall security, what is the requirement to protect APIs.
Let’s get onto this straight.
APIs are part of the ASP.NET app, but their architecture and work are pretty different, which disables them from interacting with incorporated security attributes. And for this reason, we have to create and embed our custom classes and methods for preventing cyber-attacks.
You can also refer to the official documentation provided on the Microsoft Website for this purpose. However, you can also refer to the below-provided code snippet to implement HTTPS for APIs.
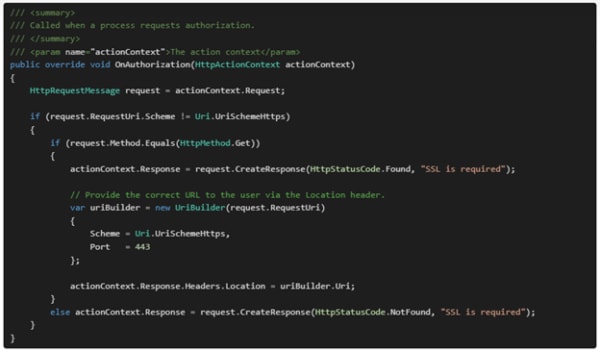
You can easily understand this code by going through the below points:
- A class RequireHttpsAttribute is derived from
- The method 0nAuhtoirzation is being overridden.
- Whenever a GET request is received, the client system will be informed about the correct URL, as it will be returned in the Location
- For any other user request except GET, a message will be displayed to the client containing the text “SSL is required.”
- Also, if any client tries to get access through HTTP, it will show a Bad request instead of redirecting the user.
This code has been mainly designed for .NET Core applications, and you create similar code for your ASP.NET solutions by deriving ApiRequireHttpsAttribute from RequireHttpsAttribute class.
Conclusion
ASP.NET comprises built-in security mechanisms, especially UseHttpsRedirection, enabling the HTTPS protocol for securely sharing the data between server and client systems. However, a developer must change the filter code in the pre-defined classes in the .NET Core architecture to allow Redirection.
In addition, this middleware is an essential component of any ASP.NET application and can be configured by modifying the filter function and adjusting the rewrite code block in the IIS. Therefore, a developer should always focus on this part while developing the solution, and it must be tested before the final deployment to ensure data integrity to each user.